One of the core requirements of CCTV networks is the requirement of network security end to end. What this means to you as a customer is a secure transfer of your video data between the camera and the recording solution or remote access.
Not all cameras are on one site in some cases you may have cameras on a building in Chester and need the cameras recording or accessible in an office in Bangor. The problem here is that putting sensitive information across the internet unsecured is a disaster waiting to happen and your video data is just as important as your customer data.
Most installers we have dealt with will install cameras and use port forwarding to give you access to your cameras remotely. This is not secure, to top this off the passwords are usually very poor at best making it very likely for your hardware to be accessed by people you do not want accessing it.
Port Forwarding
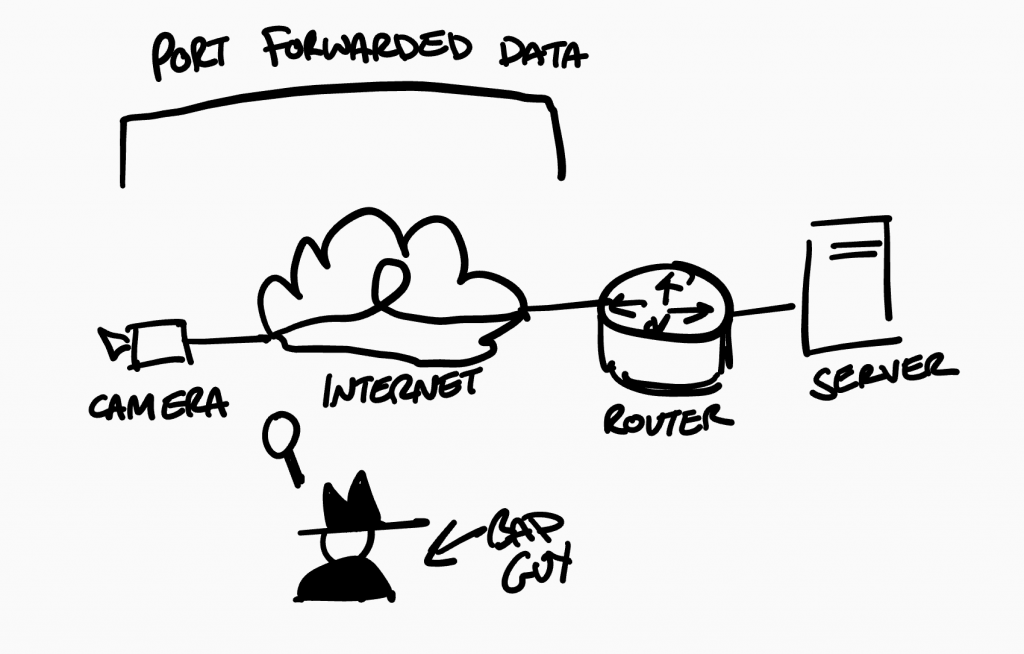
Port forwarding has its place but not for a camera network like your customer data you do not want someone having access to your cameras as they can easily gain vital information about when and where you are or even gain access to your customer data using one device to access another.
You could limit access to your forwarded traffic but there are still risks you are still forwarding data across the internet.
Solutions
VPN’s and internal security
One way to deal with this problem is to make sure the data is encapsulated in a tunnel you may know as a VPN or Virtual Private Network. There are multiple options available, some easier than others to deploy, some requiring hardware (new routers or firewalls) and some more secure than others.
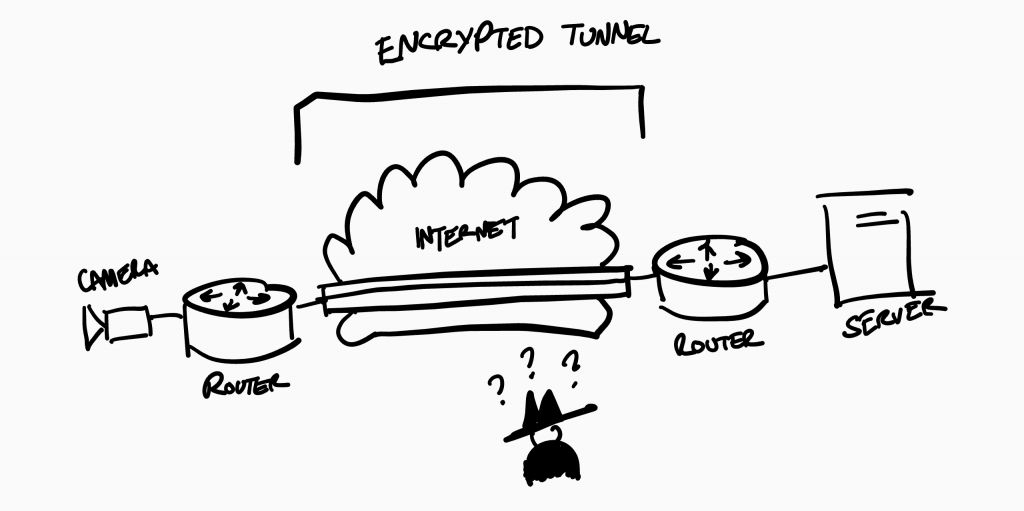
Our preferred solution is to set up VPN tunnels between sites and in some cases If required internally as well but the use of a VLAN and an ACL list should do the trick with port security enabled on any port to be sure to limit any chances of someone tampering the network to gain access. And finally a proper monitoring system to monitor all this equipment with scripts setup to send emails and alerts on any changes that have occurred.
We know this is very simplified but from what we have seen over the years with camera networks being accessed by others to do whatever they want. This is why things like port forwarding should never be used in the case of CCTV. Do not get us wrong there are uses for port forwarding like self hosting a web server or service where it can be beneficial but the general rule when it comes to CCTV networks limit the access required, CCTV NVR’s are not designed for network security first it was very much an after thought.
The Hypothetical Scenario

Here is a hypothetical scenario, you have your NVR port forwarded for your hypothetical coffee shop with no major issue but you also offer a free wifi service. Again no issue really but here is the problem our hacker wants to gain access to your coffee shop for “Free” coffee.. This sort of thing does happen and its starting to be more common.
lets get into the scenario and what are the likely steps that our Bad Guy is going to likely todo and after this lets look at finding out what we can do to
The 4 steps
Step one: first he will need to find out what your IP address (often called a WAN address, Public Address or Internet Address) is. well he knows you offer free wifi!

So he connects to your free wifi and does a quick google search. Whats my IP and right at the top of the search comes back with an IP Address. alot of search engines return your IP address as its fairly requested search and very handy if you are being a little lazy or forgetful.
Step Two: Port scanning, this involves a bit of software like nmap which is a powerful tool to scan networks. We use it to make sure there are no “leaks” in a network. But it can be used to find vulnerabilities in a network for someone to use. It will also help in findout what type of equipment our bad guy is going to come access or want to access.
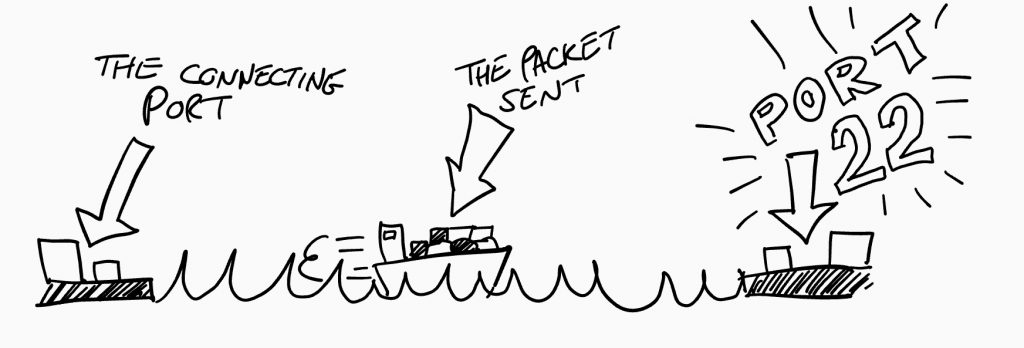
In this case the person who set up the Port forwarding was a little silly and forwarded ports 22,80,443, 8000 to a NVR (Network Camera Video Recorder).
Notes: Ports (sort of) explained: Think of it like ships docking in a port, it needs a port to drop off its load but your load is dependant on that port, so you want to access port 22 which is a port used for SSH (Secure Shell) access. To access the port using some form of software in this case port that's sent the ship, in this case terminal software like Putty.
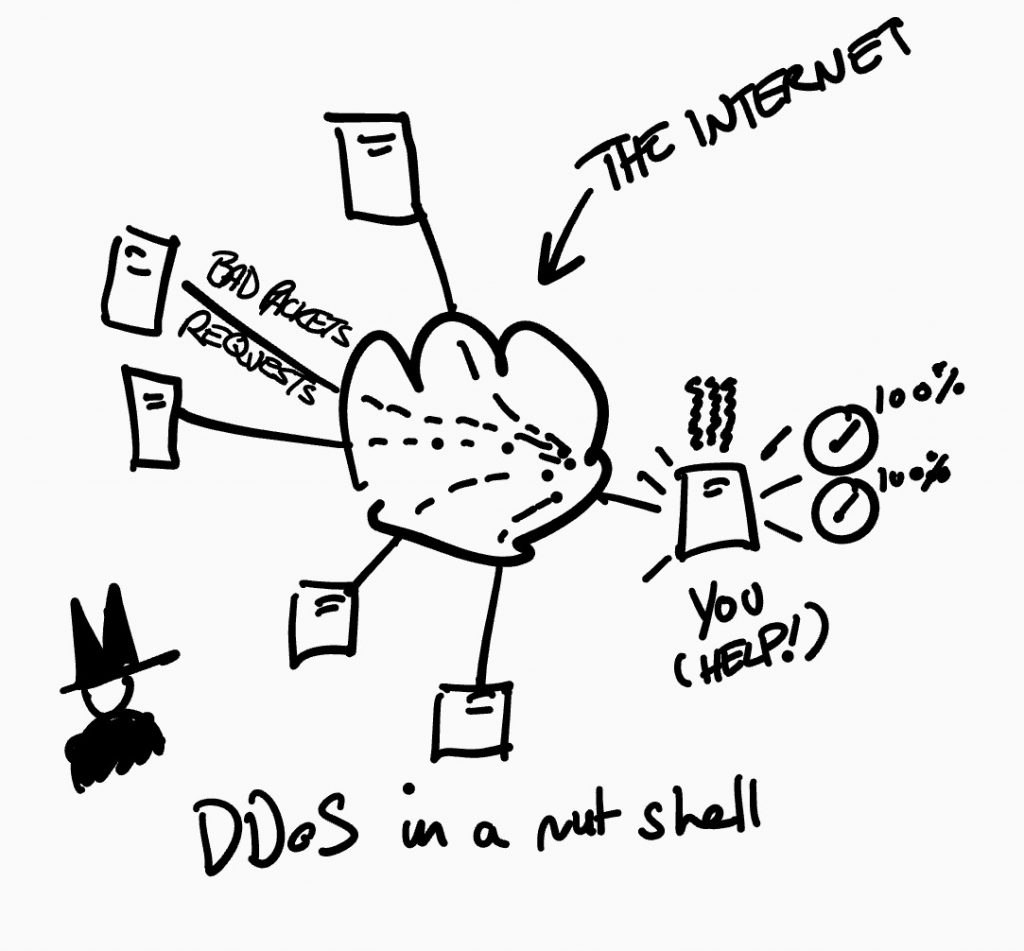
Step Three: now depending on how smart our Bad Guy is he could try to exploit a bug or try a more conventional bruteforce attack against your NVR trying to forcably access the solution or even try to DDoS (Distributed Denial of Service) the NVR and force it to crash or there is a final thing a little bit of knowlegde.
- Bug Exploiting: Simply put its finding a bug or a “feature” that gains access to the device in an unitented way if you lookup LOG4J Exploit you can see how bad that can be.
- Bruteforce: Like a man without a canopener bruteforce is slow but its effective. Many of these types of “hacks” use a already defind list passwords or random generated password to constantly tried to access a device. now this can take hours or in some cases. so if the Bad Guy had studied you for a while and knows you like football your password maybe related to this so a password list could be generated from that related information.
- DDoS: this type of attack can be brutal and long lasting but are fairly hard to setup just not impossible we will explain a bit more about DDoS at another point but if done correctly could force the NVR to crash or enable access to the device.
- Knowlegde: This one is seems sort of silly but it will make some sense. You may have put things up online like your mothers maidern name or your favourite pet so on and so on.. and as more devices ask for this sort of information for lost device passwords.. yep it happens more often than the others above.
Step Four: your in! now what? how did the bad guy get the free coffee? In his case he told the owner he could fix his problems but all it would cost is free coffee for ever! BOOOM! The bad guy gets his free coffee! ok ok ok.. usually this wouldn’t happen and technically that would make him an OK sort of guy, sort of.. but there are some who would use this access to possibly access other devices or hack other devices over time and you may find your self loosing money because someone has altered your payment terminal so on and so on..
Conclusion
Port forwarding has its place but not for CCTV or anything mission critical. We personally believe CCTV data should always be held behind a firewall and only have access via a VPN. The Internet is not a safe place and should aways be treated as such. The it comes down to CCTV you should class this as mission critical for security and safety.
